Even though we have been neglecting the News pages a bit these past few months, it does not mean nothing has happened.
So here is a short summary of awards we have won:
- Our ASPLOS paper “Who’s debugging the debuggers?” was awarded a Distinguished Paper Award!
- Victor van der Veen from won the 2021 EuroSys Roger Needham Ph.D. Award for his thesis titled “When Memory Server Not so Well: Memory Errors 30 Years Later“.
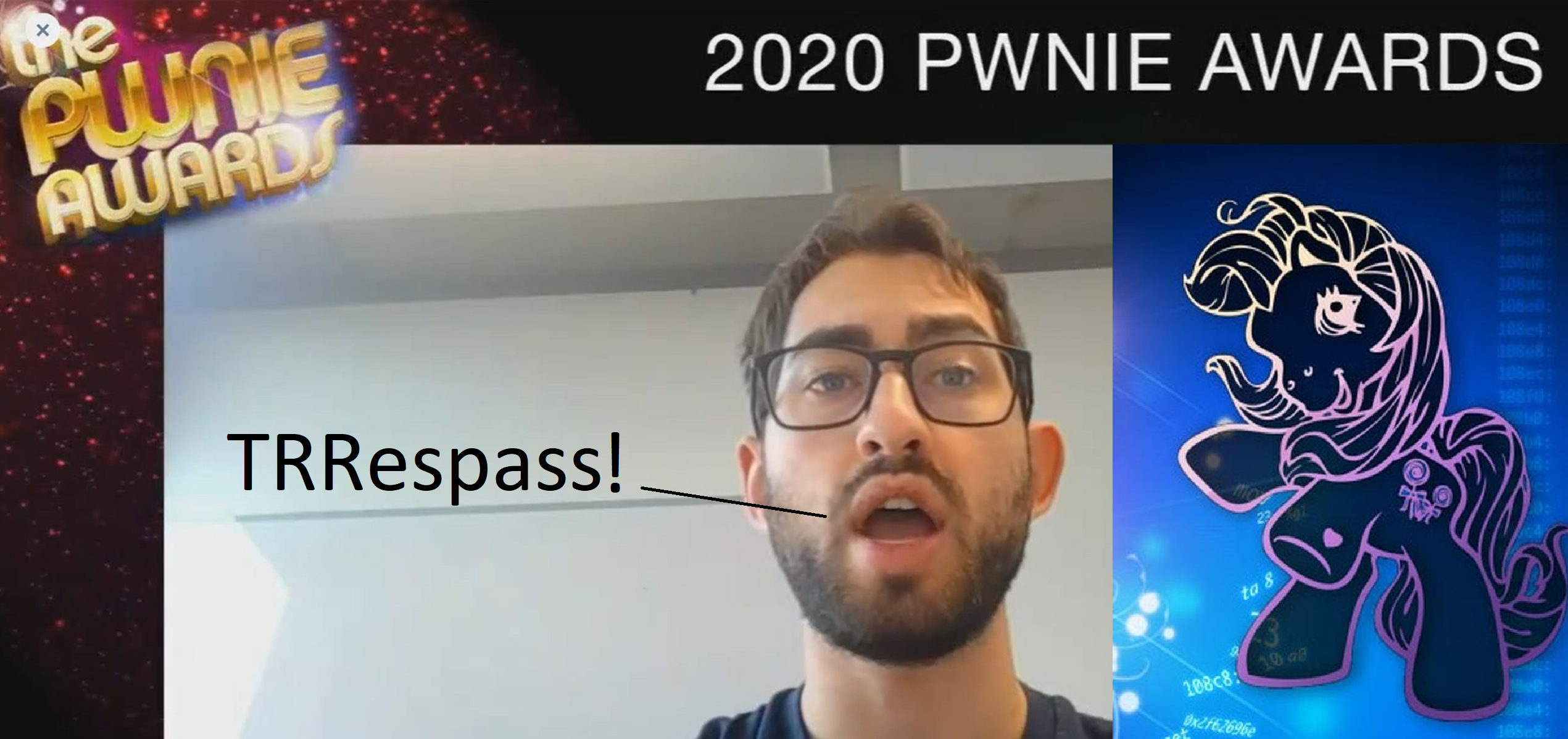
- VUsec was nominated for 6 Pwnie Awards
- Enes Goktas’ BlindSide (“hacking blind” in the Spectre era) Attack won Pwnie for Most Innovative Research (VUSec’s 5th Pwnie Awards)
- Victor van der Veen from won the 2021 DSN William C Carter Doctoral Dissertation Award for his thesis titled “When Memory Server Not so Well: Memory Errors 30 Years Later“.
- Our paper, “Rage Against the Machine Clear: A Systematic Analysis of Machine Clears and Their Implications for Transient Execution Attacks“, won Distinguished Paper Award at USENIX Security’21.