On the Limitations of Domain Isolation Against Spectre-v2 Attacks
TL;DR
We present Training Solo, the first systematic analysis of self-training Spectre-v2 attacks that break the core assumption behind domain isolation—even when implemented perfectly. Our work shows that attackers can speculatively hijack control flow within the same domain (e.g., kernel) and leak secrets across privilege boundaries, re-enabling classic Spectre-v2 scenarios without relying on powerful sandboxed environments like eBPF. We created a new test-suite to analyze the branch predictor in a self-training scenario.
We present three new classes of self-training Spectre-v2 attacks, backed by two end-to-end exploits on recent Intel CPUs that leak kernel memory at up to 17 KB/sec. Along the way, we uncovered two new hardware issues (CVE-2024-28956 and CVE-2025-24495) that completely break the domain isolation and re-enable traditional user-user, guest-guest, and even guest-host Spectre-v2 attacks.
Checkout the demo below of our ITS exploit leaking the /etc/shadow file!
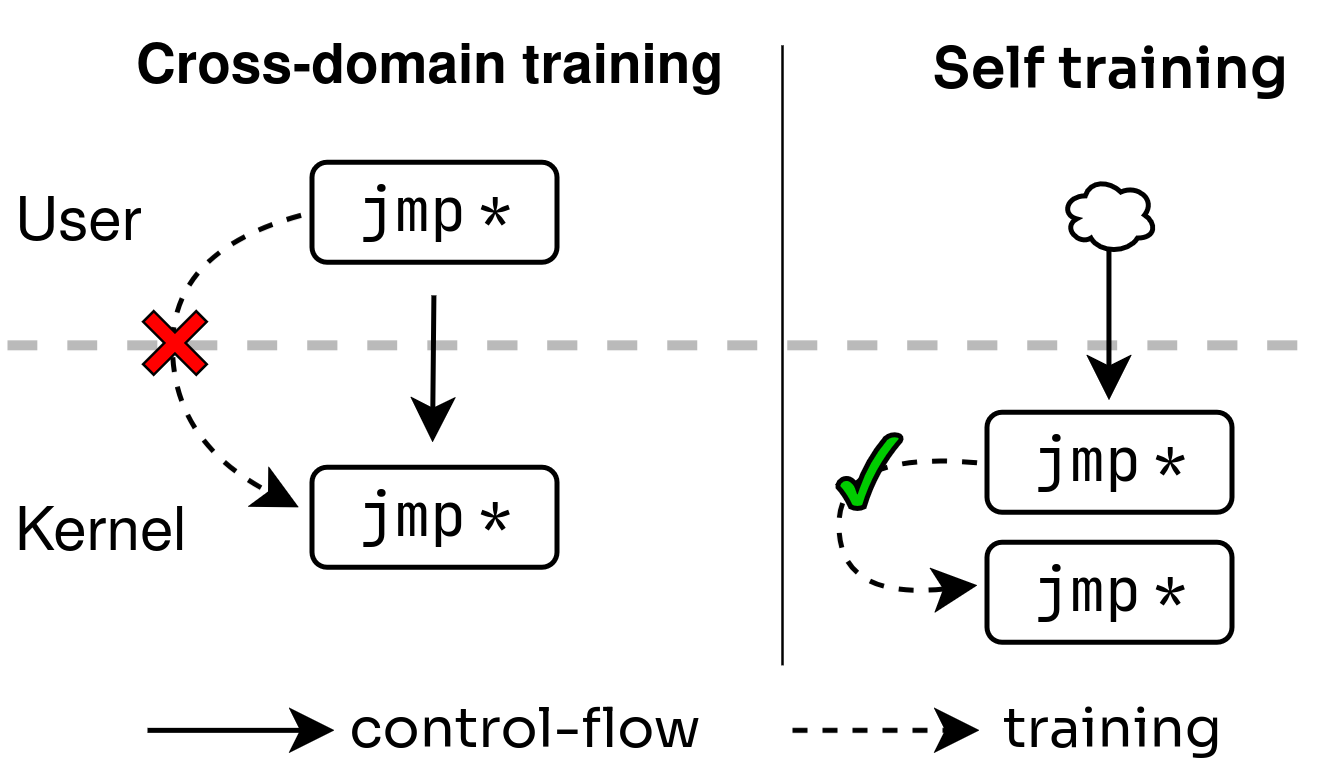
But wait—wasn’t Spectre-v2 mitigated?
Spectre-v2 has been mitigated through domain isolation techniques like IBPB, eIBRS, and BHI_NO. These defenses prevent attackers from training the indirect branch predictor with their own code (cross-domain training).
Our key insight: what if the attacker can use the code in the privilege domain for training? We show that self-training (pictured below)—where both the training and speculative execution happen inside the same privileged domain (e.g., kernel or hypervisor)—can be exploited, even with all known domain isolation protections fully enabled.
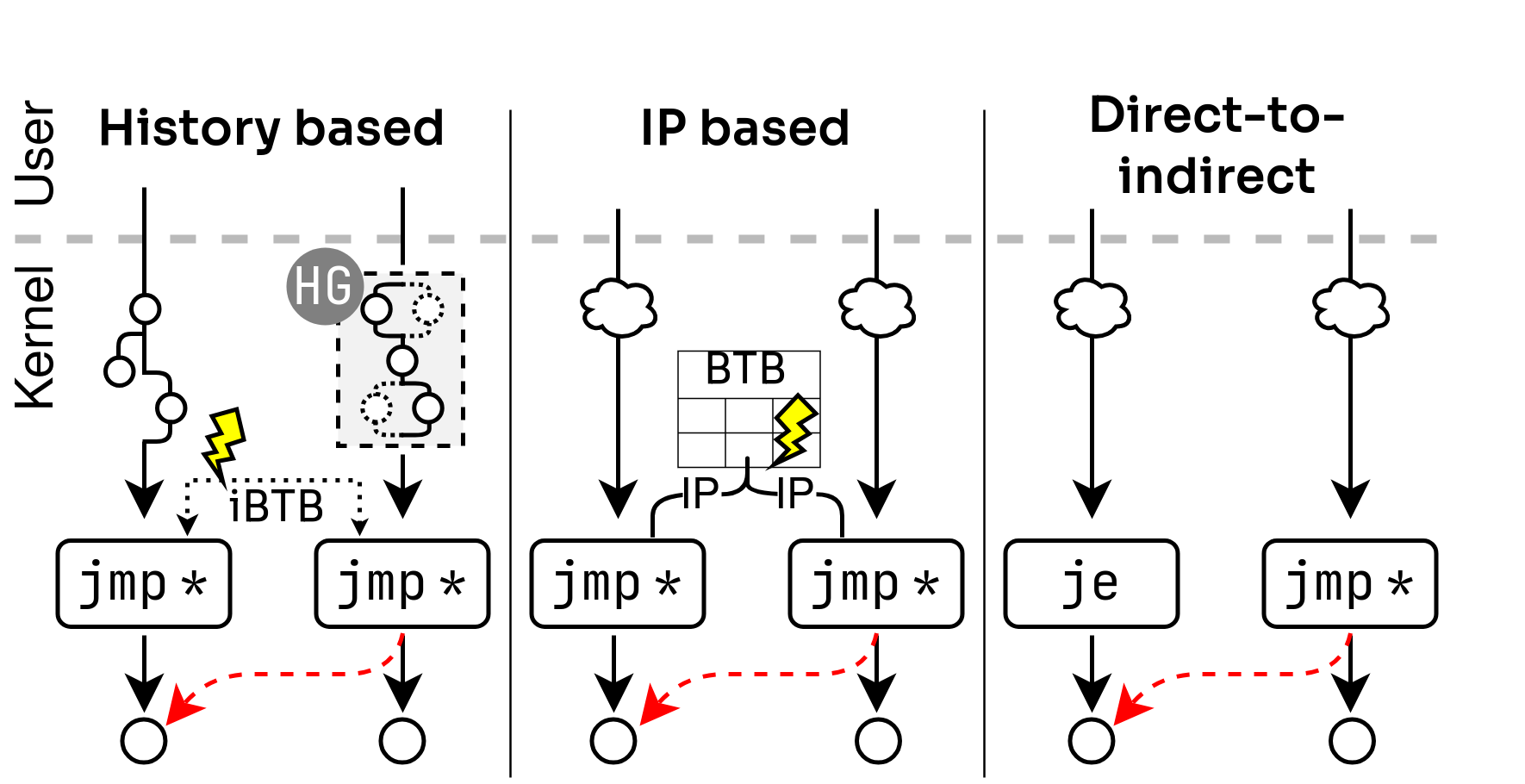
Three self-training attack classes
- History-based attacks: Bypass domain isolation by crafting in-kernel branch histories using history-crafting gadgets. We show how attackers can train the kernel via SECCOMP (cBPF, enabled by default for all users, unlike eBPF) to redirect the speculation of an indirect branch to a so-called ‘disclosure gadget’ and leak memory. We created an end-to-end exploit leaking arbitrary memory with 1.7KB/s, tested on Tiger Lake and (Intel’s latest generation) Lion Cove CPUs.
- IP-based attacks: Exploit predictable IP collisions in the branch predictor when history-based prediction is disabled. We show how attackers can force the predictor to fallback to a prediction solely based on the branch address (rather than branch history). As a consequence, two indirect branches can train each other if their address aliases (collide) in the BTB. By means of gadget analysis, we provide evidence that such attacks can be feasible in a large-scale attack scenario.
- Direct-to-indirect attacks: We discovered that on certain CPUs, direct branches can train indirect branch prediction. This behavior is caused by two hardware issues: Indirect Target Selection (ITS) (CVE-2024-28956) and a hardware issue on Lion Cove (CVE-2025-24495.). For ITS, this drastically increases the self-training attack surface. We demonstrate an end-to-end exploit leaking arbitrary kernel memory at 17 KB/sec.
Breaking implementations of domain isolation
The focus of our work is to break domain isolation by design via self-training attacks. Nevertheless, the hardware issues found by our test-suite also break the implementation of isolation, as direct branches were assumed not to be used for indirect branch training. Both issues completely break user and guest isolation and ITS also breaks hypervisor isolation, collectively re-enabling classic cross-training Spectre-v2 attacks. We created a PoC leaking hypervisor memory at 8.5 KB/s.
Summary of impact and mitigations
Our work led to multiple mitigations on current systems. We refer for a complete mitigation guidance to the vendors’ advisories. Below we give a summary of the impact of our findings.
History-based attacks
Affected: All Intel CPUs with eIBRS, including Intel’s latest generation Lion Cove which features the BHI_NO feature. Selected ARM CPUs, see vendor website.
- New x86 instruction: Intel created a new instruction IBHF (Indirect Branch History Fence) which can be placed after history-crafting gadgets, shipped via a micro-code update for certain CPUs. For older CPUs, Intel recommends using a software BHB-clearance sequence.
Indirect Target Selection (ITS) (CVE-2024-28956)
Affected: Multiple Intel CPU generations (i.e., Intel Core 9th-11th, Intel Xeon 2nd-3rd). Please refer to Intel’s advisory for a complete list.
- New indirect branch thunks: New indirect branch thunks have been developed by Intel and Linux kernel engineers which places all indirect branches on the upper half of the cache line. As only indirect branches present on the lower half of a cache line are vulnerable, this effectively mitigates self-training ITS and guest-hypervisor attacks.
- IBPB micro-code update: Intel published a micro-code update to fix the IBPB bypass.
Lion Cove BPU issue (CVE-2025-24495)
Affected: Intel CPUs with Lion Cove core (Lunar Lake / Arrow Lake)
- IBPB micro-code update: Intel published a micro-code update to fix the IBPB bypass.
Technical Contributions
- New test suite to systematically evaluate branch predictors across CPU microarchitectures.
- Extensive reverse engineering of prediction behavior across Intel generations.
- Open-source tooling, test cases, and PoC exploits: https://github.com/vusec/training-solo
FAQ
What’s new about these attacks?
Unlike previous Spectre-v2 attacks, “Training Solo” shows how to bypass (even perfect) domain isolation without needing to cross privilege boundaries. We re-enable Spectre-v2 attacks from entirely within the victim domain.
Is my system affected?
If your CPU is affected by Spectre v2, it is also affected by these new variants. Even systems with all known mitigations enabled may be vulnerable until vendor patches are applied.
How do I protect my system?
Update your system firmware and OS as soon as vendor patches are available. Intel has released guidance and microcode updates. ARM has released guidance. The Linux kernel has released a number of patches.
Are there other independent finders?
We’re not aware of other independent finders. However, others did build on our work. In response to our findings, Intel researchers further triaged our direct-to-indirect collisions (ITS) and shared their isolation-breaking findings with us. See the Intel ITS guidance for details. In response to our findings, Google researchers described potential native gadgets to induce history collisions in the Linux kernel without cBPF. See the Google Security Research project for more details.
More details
The “Training Solo” paper is accepted for publication at the 46th IEEE Symposium on Security and Privacy (presentation on May 14). Checkout the paper and code (linked below).
Acknowledgements
We would like to thank the anonymous reviewers for their valuable feedback. We also thank Intel researchers for comprehensively triaging ITS in response to our disclosure and for sharing their isolation-break findings with us. This work was supported by Intel Corporation through the “Allocamelus” project, by NWO through project “INTERSECT” and the Dutch Prize for ICT research, and by the European Union’s Horizon Europe programme under grant agreement No. 101120962 (“Rescale”).
